Table of Contents
- Executive Summary
- AAS Sector Brief
- Decision Criteria Analysis
- Analyst’s Outlook
- Methodology
- About GigaOm
- Copyright
1. Executive Summary
Modern applications are composed of the application itself and the application programming interfaces (APIs) that represent programmatic access to application subsystems. Recent trends in application development—including API-first approaches, service-oriented architectures, and microservices—have elevated the status of APIs as critical components of today’s applications.
In practice, this means many applications are now being developed as collections of API calls. An application is often some UI code and a collection of back-end APIs. The increasing use of containers only exacerbates this division. Indeed, microservices are largely enabled by container architectures. As a result, modern application security must address protecting both of these unique access points—front-end UI and back-end APIs—to protect the entire application.
Traditionally, application security and API security were viewed as totally different areas. However, the needs of the market have driven them together because, generally, one is not deployed without the other. Application and API security (AAS) encompasses both of these concerns as a single service. This has created some interesting overlap, as AAS is traditionally purchased and still largely used by IT security teams, but DevOps teams have an increasing interest and stake as they take on greater involvement in infrastructure and security.
This report is focused on universal application protection, which includes protecting applications traditionally, as with a web application firewall (WAF), as well as protecting APIs the way security API management products do. For the runtime protection portion of products in this space, the report also considers what new and unique protection might be offered based on the merging of the application and API security fields. In addition, this report also considers the increasing use of artificial intelligence (AI) and machine learning (ML) to implement features such as runtime application self-protection (RASP) via next-generation firewalls (NGFWs). At this time, AI is driving most of the changes in this technology space, as in other security- and testing-focused spaces.
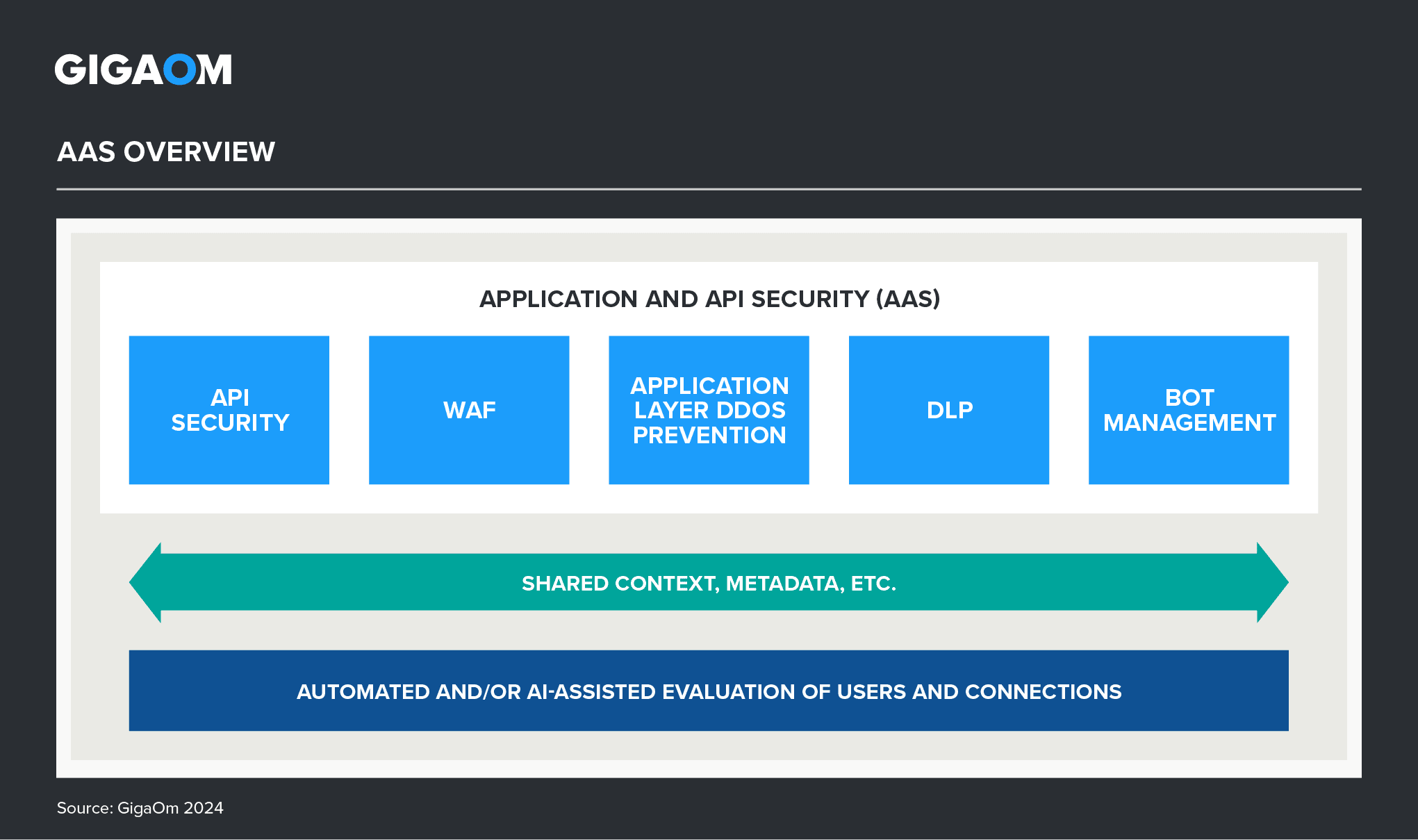
Figure 1. AAS Overview
AAS solutions today need to protect applications and their underlying APIs not only from traditional attacks like SQL injection but also from more subtle attacks that may include several stages and different attack vectors all in one. The tools must be adaptable enough to protect modern digital applications across the range of their architectures and deployment environments. The ability to work with the standard reporting and processing tools of the modern enterprise is vital.
This technology space is closely related to API security, and organizations that have a WAF or NGFW implementation that they are happy with should consider those solutions. Note that some development security solutions also offer real-time protection, and organizations should consider where to place that functionality.
Business Imperative
Attacks are increasing against any application exposed to the world, and those attacks are increasingly automated, with AI being used to evaluate weaknesses in specifically targeted organizations and attack responses. Protecting both applications and APIs that are accessible to the world is imperative and drives the adoption of comprehensive application security tools that include API security. Organizations that are happy with their WAF or NGFW might be happy with API security tools, and those with solid API security might want to fill the gap with an NGFW. However, in both scenarios, the result is similar to implementing a single AAS solution. Organizations looking to implement or replace both API security and WAF functionality will be best served by considering the vendors in the AAS space.
Sector Adoption Score
To help executives and decision-makers assess the potential impact and value of an AAS solution deployment to the business, this GigaOm Key Criteria report provides a structured assessment of the sector across five factors: benefit, maturity, urgency, impact, and effort. By scoring each factor based on how strongly it compels or deters adoption of an AAS solution, we provide an overall Sector Adoption Score (Figure 2) of 3.8 out of 5, with 5 indicating the strongest possible recommendation to adopt. This indicates that an AAS solution is a credible candidate for deployment and worthy of thoughtful consideration.
The factors contributing to the Sector Adoption Score for AAS are explained in more detail in the Sector Brief section that follows.
Key Criteria for Evaluating AAS Solutions
Sector Adoption Score
Figure 2. Sector Adoption Score for AAS
This is the third year that GigaOm has reported on the AAS space in the context of our Key Criteria and Radar reports. This report builds on our previous analysis and considers how the market has evolved over the last year.
This GigaOm Key Criteria report highlights the capabilities (table stakes, key features, and emerging features) and nonfunctional requirements (business criteria) for selecting an effective AAS solution. The companion GigaOm Radar report identifies vendors and products that excel in those decision criteria. Together, these reports provide an overview of the market, identify leading AAS offerings, and help decision-makers evaluate these solutions so they can make a more informed investment decision.
GIGAOM KEY CRITERIA AND RADAR REPORTS
The GigaOm Key Criteria report provides a detailed decision framework for IT and executive leadership assessing enterprise technologies. Each report defines relevant functional and nonfunctional aspects of solutions in a sector. The Key Criteria report informs the GigaOm Radar report, which provides a forward-looking assessment of vendor solutions in the sector.